The Essence of Data Activity Monitoring (DAM)
Introduction
Data Activity Monitoring (DAM) is a crucial component of modern data security and compliance strategies. It serves as a sentinel for organizations, safeguarding sensitive information against unauthorized access, breaches, or misuse.
What is Data Activity Monitoring?
Data Activity Monitoring (DAM) is a proactive cybersecurity approach designed to track, monitor, and analyze the actions performed on an organization's data assets. By recording and analyzing data-related activities, DAM solutions provide real-time insights into potential threats and anomalies, giving security teams a chance to respond swiftly and prevent data breaches.
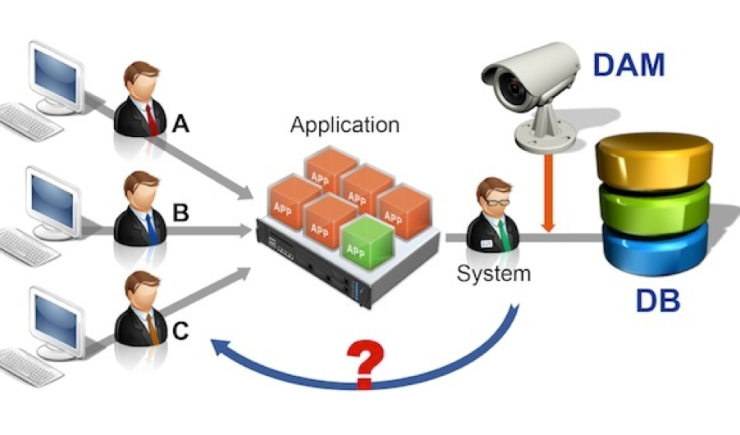
How DAM works
DAM operates on the principle of continuous monitoring, analyzing data activity throughout an organization's IT infrastructure. It involves the deployment of specialized software agents, sensors, or log collectors that work in harmony to gather comprehensive data activity information.
The collected data is then fed into a centralized monitoring platform, where it undergoes analysis and correlation. DAM employs various techniques, such as data classification, user behavior analytics, and anomaly detection, to identify patterns indicative of malicious or unauthorized actions.
Why use Data Activity Monitoring?
1) Enhanced Data Security: DAM provides a proactive defense mechanism against data breaches and insider threats. It enables organizations to identify potential risks promptly and take immediate action to prevent unauthorized access.
2) Regulatory Compliance: In an era of stringent data protection regulations, DAM helps organizations remain compliant with industry standards (e.g., GDPR, HIPAA) by ensuring data security, privacy, and auditing requirements are met.
3) Insider Threat Detection: Employees with legitimate access to data can sometimes become unintentional or malicious threats. DAM helps in identifying unusual user behavior patterns, detecting suspicious activities, and preventing data exfiltration.
4) Incident Response and Forensics: In the event of a security incident, DAM provides a valuable source of information for post-incident analysis, aiding in the investigation and recovery process.
5) Business Insights: DAM's data analytics capabilities can offer valuable insights into data usage patterns, helping organizations optimize their processes, improve efficiency, and identify areas for improvement.
Notable Solutions
1) IBM Security Guardium: IBM's DAM solution offers a comprehensive suite of data security capabilities, including real-time monitoring, data classification, and automated compliance reporting.
2) Splunk Enterprise Security: Splunk's DAM platform leverages machine learning algorithms to detect anomalous activities, enabling security teams to respond quickly to potential threats.
3) McAfee Database Security: McAfee's DAM solution focuses on safeguarding critical databases, offering vulnerability assessment, database encryption, and activity monitoring features.
Conclusion
Data Activity Monitoring (DAM) has evolved into an indispensable tool for modern organizations looking to safeguard their valuable data assets. By continuously monitoring and analyzing data activities, DAM solutions empower businesses to thwart potential threats, ensure regulatory compliance, and gain valuable insights into their data usage patterns. As data continues to be a cornerstone of modern enterprises, implementing DAM becomes an imperative step towards bolstering overall cybersecurity posture.
